Beware of New iMessage Scams: Scammers Found a Sneaky Way to Bypass Apple Protections!
2025-01-14
Author: Lok
What You Need to Know About the USB-C Vulnerability
The USB-C controller chip, known as ACE3, was introduced in Apple’s latest iPhones in 2023. Security researcher Thomas Roth revealed that, while they managed to exploit this chip under laboratory conditions to gain code execution, real-world applications are considerably challenging. It requires direct physical access to the device, making it improbable for most attackers to use in the wild.
In a theoretical scenario, an attacker could gain complete control over an iPhone if they successfully manipulate the ACE3 chip. However, the complexity of this method led both Apple and Roth to conclude that it isn’t a realistic threat to everyday users.
The Sneaky Scam: How Scammers Outsmart Apple’s Protections
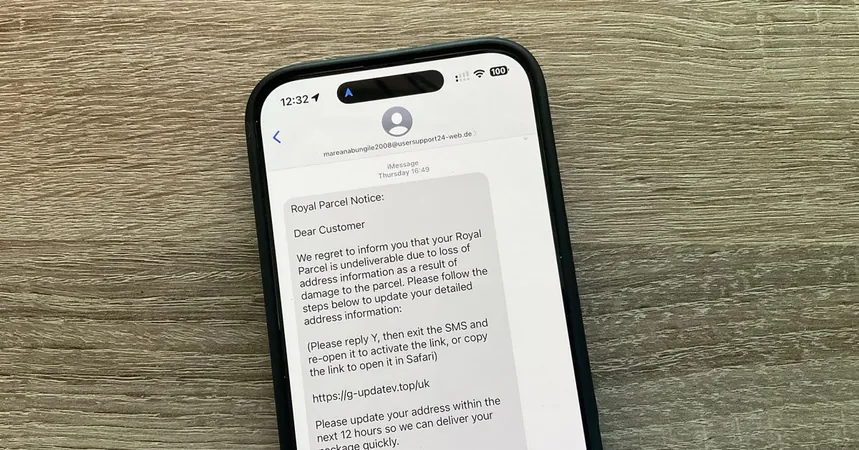
While the USB-C vulnerability might not pose an imminent risk, iPhone users are facing a growing threat from a new wave of scams, particularly through iMessage. Scammers have become increasingly savvy, utilizing SMS and iMessages to distribute malicious links aimed at phishing for personal information or installing malware.
Apple's automatic protection mechanism disables links in messages from unknown senders that haven’t been previously engaged, rendering them harmless. But scammers have discovered a loophole. If they persuade you to respond—even with a simple "STOP"—the iPhone's protective barrier is removed, allowing the links to become clickable.
BleepingComputer highlighted this alarming tactic, noting a surge in "smishing" attacks (“SMS phishing”) designed to trick users into replying, thus enabling the links again. These deceptive messages often impersonate trusted entities like USPS or toll road services, prompting recipients to respond with affirmative replies like “Y,” effectively bypassing Apple’s safety measures.
How to Shield Yourself from these Scams
To protect your personal information, here are essential practices to follow:
1. **Stay Vigilant with Links**: Never click on links from unsolicited messages. Always rely on bookmarks or manually enter URLs for any site you wish to visit.
2. **Verify Sender Authenticity**: If a message seems suspicious, directly contact the company through verified channels to confirm if the communication is legitimate.
3. **Be Cautious with Replies**: Remember that engaging with a suspicious message—even with a single character—can enable harmful links.
4. **Enable Two-Factor Authentication for Apple ID**: To bolster protection, ensure your Apple ID is secured with two-factor authentication, making it more difficult for scammers to gain unauthorized access.
In an age where technology offers convenience, it also opens the door to risks. Stay informed and vigilant to navigate these potential threats effectively!



 Brasil (PT)
Brasil (PT)
 Canada (EN)
Canada (EN)
 Chile (ES)
Chile (ES)
 Česko (CS)
Česko (CS)
 대한민국 (KO)
대한민국 (KO)
 España (ES)
España (ES)
 France (FR)
France (FR)
 Hong Kong (EN)
Hong Kong (EN)
 Italia (IT)
Italia (IT)
 日本 (JA)
日本 (JA)
 Magyarország (HU)
Magyarország (HU)
 Norge (NO)
Norge (NO)
 Polska (PL)
Polska (PL)
 Schweiz (DE)
Schweiz (DE)
 Singapore (EN)
Singapore (EN)
 Sverige (SV)
Sverige (SV)
 Suomi (FI)
Suomi (FI)
 Türkiye (TR)
Türkiye (TR)
 الإمارات العربية المتحدة (AR)
الإمارات العربية المتحدة (AR)