Shocking Discovery: WPA3 Network Passwords Compromised Through MITM Attacks and Deceptive Techniques!
2024-12-23
Author: John Tan
Introduction
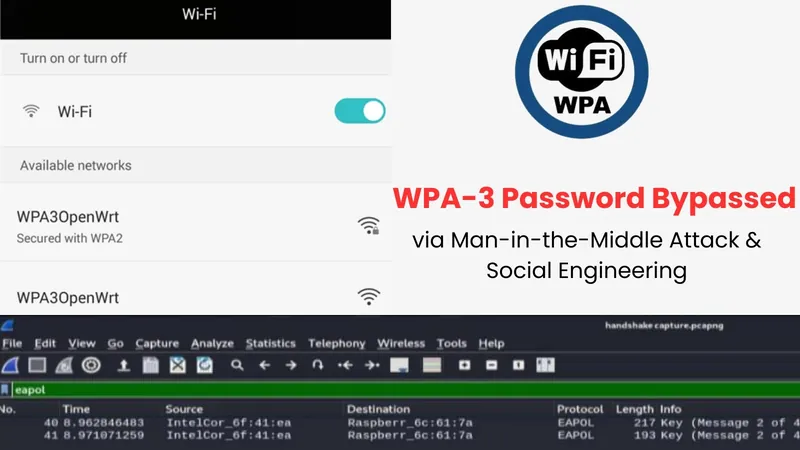
In a groundbreaking study that has sent shockwaves through the cybersecurity community, researchers from the University of the West Indies have managed to bypass the Wi-Fi Protected Access 3 (WPA3) protocol. Using a clever blend of Man-in-the-Middle (MITM) attacks and social engineering tactics, the team uncovered serious vulnerabilities in what was supposed to be the most secure wireless security standard to date.
Background on WPA3
WPA3 was unleashed in 2018 to remedy the shortcomings of its predecessor, WPA2, by providing stronger protection for Wi-Fi networks. Notably, it features the Simultaneous Authentication of Equals (SAE) protocol, which was designed to thwart offline dictionary attacks, but the researchers revealed that the protocol’s transition mode—originally intended to maintain compatibility with older WPA2 devices—is a critical flaw.
Methodology
The researchers, Kyle Chadee, Wayne Goodridge, and Koffka Khan, executed a downgrade attack, managing to capture part of the WPA3 handshake and subsequently employing social engineering to retrieve the network password. Their shocking methodology unfolded in three main stages:
1. Handshake Capture
The team initiated a downgrade attack to capture critical data from the WPA3 handshake.
2. Deauthentication
They forcibly logged users out of the legitimate WPA3 network, making their fake network more attractive.
3. Evil Twin Access Point
Using a Raspberry Pi, the researchers created a rogue access point replete with a captive portal. Unsuspecting users who attempted to connect were tricked into entering their Wi-Fi password, which was cross-verified against the previously captured handshake.
Tools and Techniques
Utilizing tools like Airgeddon, they demonstrated just how easily users can fall victim to well-crafted schemes. The attack highlighted a significant oversight: many users may not have enabled Protected Management Frames, a setting that offers an important layer of security.
Surprising Discoveries
In a surprising twist, the researchers found that some devices failed to connect to WPA3 transition networks, challenging claims from the Wi-Fi Alliance about seamless backward compatibility. This revelation raises further concerns, emphasizing the need for better consumer information regarding device capabilities when transitioning to newer security protocols.
Reactions from Experts
Experts in the cybersecurity field are sounding the alarm, calling for a thorough investigation into these newly discovered vulnerabilities. As Wi-Fi networks are integral to both personal and business domains, the stakes are higher than ever.
Conclusion
The implications of this study remind us that even the most advanced security measures can be undone by attackers employing both technical prowess and psychological manipulation. As the adoption of WPA3 widens, it's critical that both users and manufacturers stay alert and adopt proactive measures to defend against these potential threats.
Future Investigations
As a follow-up to this groundbreaking study, the research team plans to conduct further investigations into other vulnerabilities within WPA3 and devise countermeasures, reinforcing the relentless struggle between cybersecurity defenders and malicious actors in our increasingly interconnected world. Users, beware: The battle for virtual safety is far from over!




 Brasil (PT)
Brasil (PT)
 Canada (EN)
Canada (EN)
 Chile (ES)
Chile (ES)
 España (ES)
España (ES)
 France (FR)
France (FR)
 Hong Kong (EN)
Hong Kong (EN)
 Italia (IT)
Italia (IT)
 日本 (JA)
日本 (JA)
 Magyarország (HU)
Magyarország (HU)
 Norge (NO)
Norge (NO)
 Polska (PL)
Polska (PL)
 Schweiz (DE)
Schweiz (DE)
 Singapore (EN)
Singapore (EN)
 Sverige (SV)
Sverige (SV)
 Suomi (FI)
Suomi (FI)
 Türkiye (TR)
Türkiye (TR)