Unveiling the New Threat: Gelsemium's WolfsBane Linux Backdoor Targeting Asia
2024-11-23
Author: Arjun
Introduction
Recent cybersecurity reports reveal that the China-linked Advanced Persistent Threat (APT) group known as Gelsemium has commenced deployment of a sophisticated new Linux backdoor dubbed *WolfsBane*. This alarming development primarily impacts organizations across East and Southeast Asia, specifically targeting entities in Taiwan, the Philippines, and Singapore.
WolfsBane and FireWood
Cybersecurity experts at ESET have pinpointed *WolfsBane* as part of a broader strategy by Gelsemium, revealing that this backdoor is not an isolated tool. The group has also experimented with another Linux backdoor named *FireWood*, though it remains uncertain whether *FireWood* is directly associated with Gelsemium or if it is commonly used across various China-linked APT groups. Analysts have low confidence in directly linking *FireWood* to Gelsemium’s other tools.
Similarities to Windows Tools
Both *WolfsBane* and *FireWood* exhibit similarities to Gelsemium’s Windows-based espionage tools, which have traditionally focused on data exfiltration while attempting to remain undetected. The group’s pivot to Linux systems signals a strategic shift likely driven by advancements in Windows security measures. Experts note that the adoption of endpoint detection and response (EDR) tools and changes in Microsoft’s security policies—such as disabling Visual Basic for Applications (VBA) macros by default—are prompting adversaries to explore new vulnerabilities, specifically those present in Linux-based systems that operate on the internet.
Increased Focus on Linux Vulnerabilities
ESET mentions, "The increased sophistication in Windows defenses has led cybercriminals to seek alternative attack vectors," indicating that vulnerabilities in internet-facing Linux systems are becoming prime targets for threat actors.
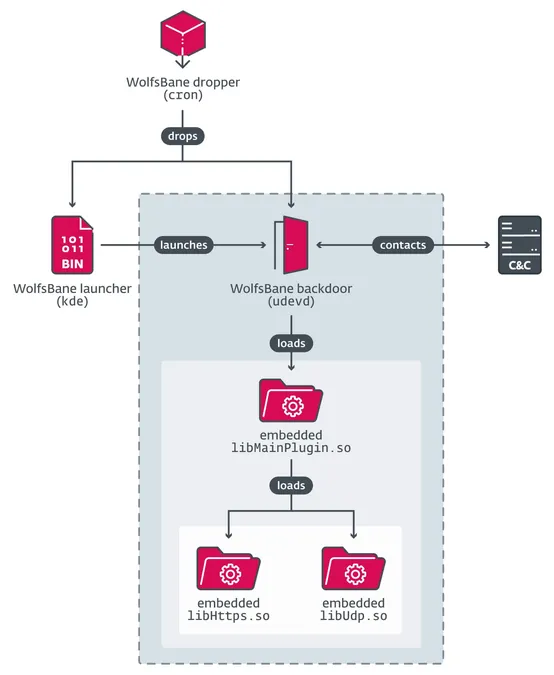
Technical Analysis of WolfsBane
*WolfsBane* bears a striking resemblance to *Gelsevirine*, its Windows counterpart. The design similarities are evident in their network communication methods, where both deploy custom libraries and even share the same typographical errors in coding, particularly in session initiation function names. They both utilize a unique command execution mechanism, wherein commands are mapped from hashed command names to specific function pointers—demonstrating a cohesive method within Gelsemium's toolset.
Configuration Structure
Moreover, the configuration structure of *WolfsBane* and *Gelsevirine* shows notable parallels, with the Linux version incorporating some different fields while retaining many common nomenclatures. Interestingly, certain values, like the "pluginkey," align perfectly with those found in *Gelsevirine* samples dating back to 2019. This consistency across platforms suggests a robust developmental framework utilized by Gelsemium.
Infiltration Methods
The precise method of Gelsemium's initial infiltration remains shrouded in mystery, but researchers believe attackers likely exploited a presently undisclosed vulnerability in web applications, enabling them to place web shells for persistent access. Subsequently, they delivered the *WolfsBane* backdoor through a dropper mechanism.
Conclusion
As the cybersecurity landscape evolves, adversaries are compelled to pivot their strategies to exploit weaker links. As noted in the report, "The vulnerabilities in internet-facing infrastructures, especially those on Linux systems, are escalating in importance as prime targets." As cyber threats grow in sophistication and adaptability, vigilance remains essential for organizations using Linux systems, as they may become the next battleground in an ever-evolving cyber warfare landscape.
Stay informed on cybersecurity advancements and insights! Follow me on Twitter for real-time updates.





 Brasil (PT)
Brasil (PT)
 Canada (EN)
Canada (EN)
 Chile (ES)
Chile (ES)
 España (ES)
España (ES)
 France (FR)
France (FR)
 Hong Kong (EN)
Hong Kong (EN)
 Italia (IT)
Italia (IT)
 日本 (JA)
日本 (JA)
 Magyarország (HU)
Magyarország (HU)
 Norge (NO)
Norge (NO)
 Polska (PL)
Polska (PL)
 Schweiz (DE)
Schweiz (DE)
 Singapore (EN)
Singapore (EN)
 Sverige (SV)
Sverige (SV)
 Suomi (FI)
Suomi (FI)
 Türkiye (TR)
Türkiye (TR)